Good afternoon to our human and bot readers out there on the big World Wide Web! I have a couple of posts today related to Model Context Protocol servers. As I am knee deep at the day job in the early planning stages of how we are going to both deploy and secure these in our healthcare system. I plan on post some blogs sometime next month on the journey and what key things I have learned along the way. In the meantime, let's jump into the first of two posts for today.
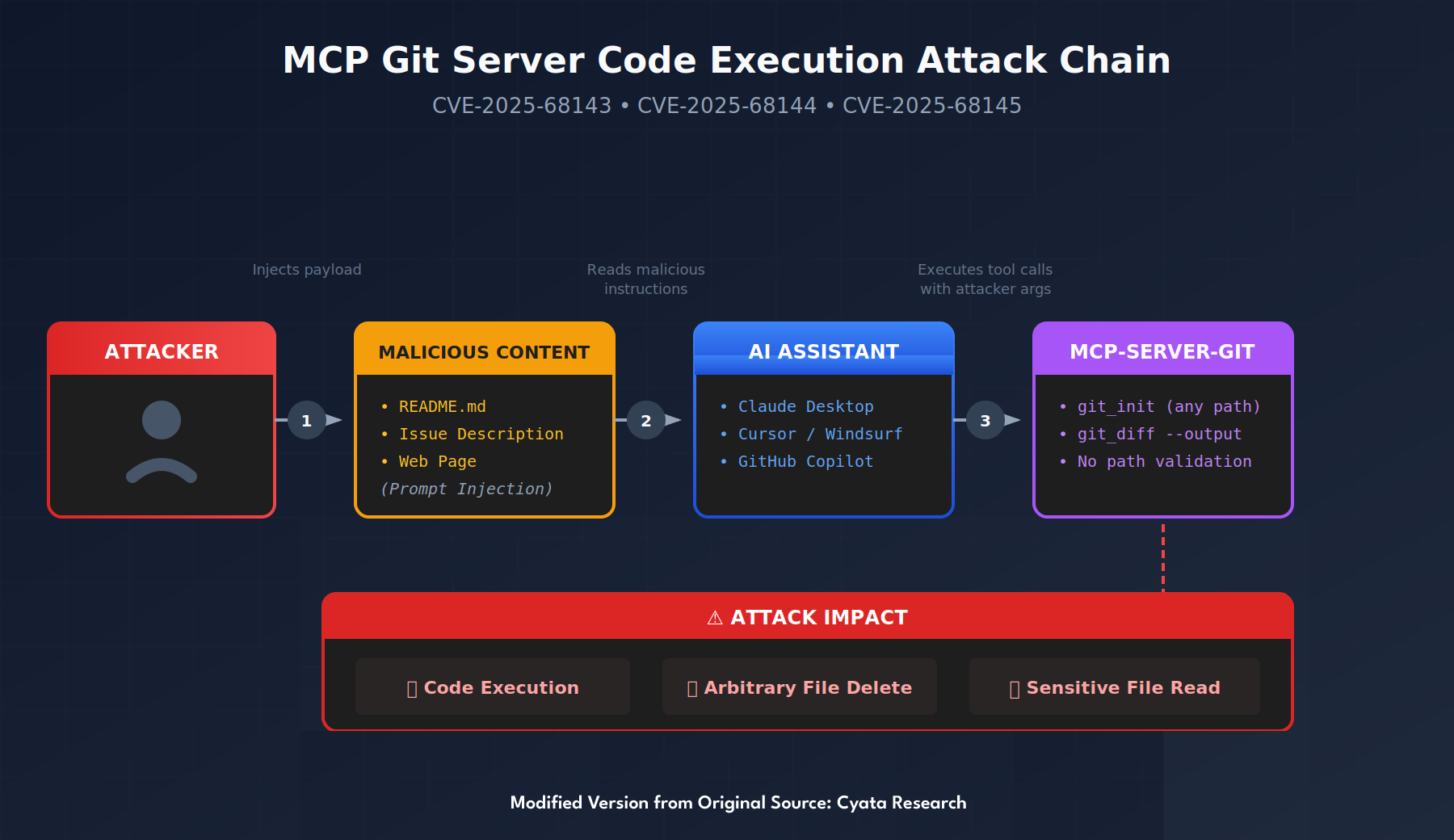
Security researchers at Cyata discovered three vulnerabilities (CVE-2025-68143, CVE-2025-68144, CVE-2025-68145) in mcp-server-git, the official Git MCP server maintained by Anthropic. What makes these findings particularly significant is that they affect the reference implementation from the creators of the Model Context Protocol itself—not a third-party integration. The vulnerabilities are exploitable through prompt injection, meaning an attacker doesn't need direct system access; they only need to influence what the AI assistant reads, such as a malicious README file, poisoned issue description, or compromised webpage.
The root cause stems from insufficient input validation. The server accepts a repo_path argument directly from tool calls without verifying it against the configured --repository flag, allowing access to any Git repository on the system. The git_init tool has the same weakness, enabling attackers to initialize Git repositories in arbitrary directories. Perhaps most critically, the git_diff function passes its target parameter directly to the Git CLI without sanitization, enabling argument injection attacks using flags like --output to overwrite files.
When combined with filesystem write capabilities common in AI-powered IDEs (Cursor, Windsurf, GitHub Copilot), these vulnerabilities chain together for full code execution. The attack leverages Git's smudge/clean filter feature, which executes shell commands during staging operations without requiring execute permissions on any file. An attacker can create a malicious .git/config with a clean filter, then trigger code execution simply by calling git_add on a file matching the filter pattern.
Organizations using mcp-server-git should immediately update to version 2025.12.18 or later. Security teams should also audit which MCP servers run together, as combining Git and Filesystem servers significantly increases the attack surface. This research reinforces that MCP security requires careful attention to tool chaining and prompt injection defenses—the same principles healthcare organizations must apply when evaluating AI agent deployments.
Here is a diagram of the MCP Git attack flow:
Key Takeaways for Healthcare Security Teams:
- Update immediately — Versions prior to 2025.12.18 are vulnerable
- Audit MCP server combinations — Git + Filesystem together creates elevated risk
- Monitor for anomalies — Unexpected .git directories in non-repository folders may indicate compromise
- Prompt injection is the attack vector — No direct system access required; malicious content in repos, issues, or webpages is sufficient
- Reference implementations aren't immune — Even official, vendor-maintained tools require security validation
Thank you to Alessandro from Infosecurity Magazine for the heads up.
